Mail and Calendars at the MPI/CBS
Permanent Link:Summary: Find information about the institute's groupware service (email, calendars, etc.) here.
- Overview
- Getting started
- FAQ - Awareness
- FAQ - Access, Security
- How do I access the institute email account?
- How do I use encryption or digital signatures?
- Application passwords - How do I use 2FA with email/calendar software?
- Why am I sometimes logged out of the Web GUI without explanation?
- My account is suddenly inaccessible and I cannot re-login.
- I have two or more phones. Can I use either one for 2FA?
- The generated TANs don't work (anymore). What's wrong?
- What if I loose access to my TANs?
- Why do I have to use Password and/or 2FA every time I login? (How to save some time)
- FAQ - Misc
Overview
Central IT provides a Groupware service (email, calendars,...) that is accessible to all institute users. In addition to simple sending/receiving emails, there are several advanced features available:- Multi-layer calendars with integrated access to the institute's room planning.
- Easy to use Web GUI for browser access.
- Excellent backup and undelete functions
- Export feature—very useful, when you leave the institute and you want a copy of either the whole account or of specific parts.
- Two-Factor-Authentication is mandatory for this service.
Getting started
- Go to https://mail.cbs.mpg.de , log in using your institute login name and your institute password.
- Upon first login, you'll have to enable 2FA. Short: You'll need Google Authenticator. Longer: See Groupware2FaSetup.
- Find out how to connect other applications/devices to your Groupware account. You'll have to use one unique application password per application.
FAQ - Awareness
What is important to know about email in general?
Permanent Link:- Email is being used by people with malicious intend to cause damage to users and the infrastructure. It's imperative to know a thing or two about attack types.
- Email sender and receiver addresses look like this:
"John Doe" <johndoe@mailserver.domain.de>- (B1) Only the second part is actually an address. The first part is an arbitrary text . These addresses might be able to trick you:
-
"Prof. Dr. John Doe" <intern1@cbs.mpg.de>is still just an intern although he calls himself "Prof." -
"administration@cbs.mpg.de" <intern1@cbs.mpg.de>(still an intern).
-
- (B1) Only the second part is actually an address. The first part is an arbitrary text . These addresses might be able to trick you:
- (B2) You cannot be sure that the sender address is valid and was sent by the respective email account.
- An email server could make sure that all sender addresses ending with its domain (
@cbs.mpg.dein our case) are valid.
This is currently not possible on our email server because IT was mandated to support a specific service for one of the departments which requires the sender address to be forgeable. - (B3) Even if the email was actually sent from the expected mail account, you cannot be sure, the mail was sent by the owner of the account.
- It is common that users are tricked by bad people into sharing their passwords. Their email accounts are then abused to send spam, malware (e.g. viruses) or phishing emails.
- Try not to look for clues of validity in metadata but in the emails content itself. Example:
- No legit invoice comes in form of an
.exe-file. - A director is not in urgent need of Google gift cards.
- An institute user having to "validate" an email account doesn't make sense. Account validity is tied to contract data and a user management system would not trust users to update this by themself.
- A quota increase will not require you to login somewhere.
- If in doubt, use another means of communication to ask the assumed sender of the email (Phone, Whatsapp, Mivervamessenger,...). The idea is to assume that an attacker has a harder time compromising multiple communication channels at once.
- No legit invoice comes in form of an
- An email server could make sure that all sender addresses ending with its domain (
- (B4) Transport Encryption: While email is send through the internet using encrypted server-to-server connections, all parties involved (esp. email server administrators) are still able to read (and change) them in the clear.
- To prevent an email being read along the way, end-to-end encryption must be used. A digital identity necessary to receive encrypted mails can be requested at CertificateManagement .
- To prevent an email to be changed along the way, signatures must be used. A digital identity use for receiving encrypted mails can be used to sign emails as well.
- (B5) Digitally signed emails are the only reliable way for a receiver to spot forged sender addresses and to ensure the email not to be changed along the way.
- However, even with signatures you still have to carefully check sender addresses.
- These addresses ernie@emailprovider.com and ernie@еmailprovider.com are not the same. The second domainname starts with a cyrillic Ye and a user will be able to get a valid digital identity for it.
- (B6) An email can take up to three days to arrive.
- (B7) To send end-to-end encrypted mails, the receiver must have a digital identity - the sender does not need one. For signatures, it's the other way around.
- (B8) Receiving an encrypted email should in no way increase your trust in it. It just ensures that nobody can read it during transit. It doesn't tell you anything about the person who sent it. That's what signatures are for.
- Nearly all attacks on IT infrastructure occur through email, particularly through harmful attachments.
What is important to know about email in the institute?
Permanent Link:- The institute operates an on-premise email server. Emails to other institute users never leave the institute's domain of control - as long as the respective user doesn't have a forward defined.
- To mitigate attacks on IT infrastructure, several types of email attachments are blocked, see the list here. Emails carrying them are not delivered. Sender and receiver are notified immediately about each single blocking event.
- There is a size limit for receiving text emails on the institute's mail server: 25,6 MB (24.4 MiB). Attachments are not sent as text but have to be recoded for transport. The effective limit of an email containing attachments is around 18 MB (17 MiB).
- There is a spam classification and filtering system being used on the server which will try to sort out unwanted mails. If you think an email for you was lost in transit, have a look in the "Spam" folder.
- "Gray listing" is used as another spam filtering mechanism by the institute. This method doesn't effect emails sent by "normal servers" (e.g. not shady spammer mail servers) since it filters by examining mail server behavior - not by looking at properties of emails.
- There are no filtering mechanisms exceeding the ones mentioned here. If you think, an email was lost, please contact IT. Every single incident will be investigated!
I want to be extra careful. Which attack types should I look out for?
Permanent Link:There are different ways of harming you when it comes to your email account. You'll need a certain amount of understanding of the matter to be able to withstand these attacks which there are several different types of:
Malware
Malware attacks are attempts to get control over the computer of an email's receiver. There are simple cases like .exe files being sent as an attachment and more complex ones like specifically crafted emails that trigger bugs in the email software without user interaction. IT has measures in place to make both types of of malware attacks less likely. To reduce the risk as a user, the best method is to handle emails only es text which means:- Do not enable "HTML mail view" in your email program.
- Do not send rich text email (or "HTML" email). This will reduce the pressure on others to enable HTML mail view.
Spam
Spam is commercial or political advertisements being sent to your mailbox. Spam is usually just annoying and primarily an attack on your scarce time. IT has measures in place which reduce spam dramatically by exploiting the fact, that spam is against the law and the sender cannot use official mail servers to send it. These are hard facts, a service provider can look. Soft ones are a bit of a problem since someone providing a mail-like service in Germany is not really allowed to not deliver a message. Additionally, a per-account spam filter is being trained by putting spam emails manually into this folder - e.g. by hitting the "Spam" button on a Email in the mail server's Webgui or your Mail app. This method is quite powerful since each account's training dataset is different. It is therefore impossible for a spammer to optimize spam emails to circumvent all mail account's filters which would be possible, if the training would be done centrally.Phishing
Phishing emails try to get you to reveal secrets which are later abused to take control of our infrastructure without authorization, e.g. email account. These emails are not attacks on a technical level but they try to deceive you. This type of attack is not a problem as long as you- do not send any credentials via email and
- you adhere to Rule#1 ("Don't enter your passwords into websites not on servers ending with
.cbs.mpg.de").
Scam
Some bad people may try to trick you into certain actions by pretending to be someone else. Most prominent these days is the gift card scam: Someone claiming to be an authority figure, like your boss or a director, ask you to buy gift cards (e.g. from Google) and send the card details to them through email. Nothing can be done by IT to protect you against this type of attack.2FA - What is Two-Factor-Authentication? And why is it necessary?
Two-Factor-Authentication is a concept taking into account that it's less likely to compromise two kinds of credentials. Take an ATM card for example. A PIN (=knowledge) is required in addition to some object (the card) to get money. For a bad guy it's more difficult to steal just the card than stealing it and guess the PIN. For the Groupware service, a method called OATH-TOTP is being used. You require the app Google Authenticator on your phone plus an additional password that you don't have to (and should not) remember. The app will create TANs (transaction numbers) once every 30s. The transaction numbers are made of the password and the current time—no internet connection is necessary on your phone. The algorithm is widely known. Alternative OATH-TOTP apps are available—although it's recommended to use Google Authenticator for support reasons.Email software
Permanent Link:Recommended software
Email can be handled via standard protocols by a wide variety of software. However using a recommended software package ensures that IT can help you quickly, if you experience problems.| Platform/OS | Situation | Software | Reasons | Comments |
|---|---|---|---|---|
| Via any web browser | Mail access on a regular computer or Laptop | The Web GUI | No setup is required IT takes care of updates/security patches By far the best email Web GUI. |
No encryption and digital signatures can be used. On mobile devices, the regular Web GUI doesn't perform well. A special "mobile" Web GUI with a reduced feature set can be selected. |
| Android | Email access on Android phone or tablet | Fairmail | Very feature rich open source email client software from an author known for his strong pro-privacy attitude. | One time pay: EUR 5,99 (for all devices) |
| Android | Calendar/Contacts access on phone or tablet | Dav5X | Simple and functional, tested with our Mailserver | One time pay: EUR 5,99 (for all devices) Dav5X is not a calendar software but a sync plugin. A calendar software is included in Android, various other ones can be installed/bought. |
| Linux, Windows, macOS | Email access on a regular computer or laptop, offline use required. | Thunderbird | Thunderbird is freely available and behaves identically on all platforms. Thunderbird's certificate store (used during email signing and encryption) is independent of the OS and therefore not prone to OS-specific quirks. | |
| iPhone, iPad | Email, Calendar and contacts | IOS included software | No known problems | Setup is possible with high degree of automation. Go to Groupware for detailled instructions. |
Blacklist - do not use this software!
These software packages must not be used! This is usually because of mail content being sent to unsafe countries or to services which do not provide adequate data protection.| Blacklistet software | Explanation |
|---|---|
| BlueMail | BlueMail collects and processes your account information, when you setup instant push notification. In practice this means, they sync your account credentials to hosts inside the Amazon Cloud, and access your email from there. |
| Craigpark | The use of Apps related to Craigpark Limited and Mail.ru, for example Email App for Outlook & others, Email App for Yahoo! & others, Univeral Email and other derivatives is prohibited due to their use of Cloud Services |
| Edison Mail | Edison Mail for Windows 10 and Android, accesses your account and message directly through your device as well as intermittently through Amazon-hosted cloud servers. |
| Gmail Web service | Do not use this in the Gmail WebUI: "Gear wheel"/"Accounts and Import"/"Import mail and contacts.". The Gmail app on android is perfectly fine. |
| Newton | Newton Mail for Android accesses your account data and personal information similar to Editon Mail through your device and Amazon Cloud services. |
| Outlook for iOS and Android | Starting with the "New Outlook for Windows" (successor of Windows Mail) and newer version of Outlook for Mac 16, Microsoft will openly offer or force you to setup cloud sync "for [a] experience". With this feature enabled, Microsoft will sync your credentials and messages to their cloud and everything on your client will exclusively happen though their cloud. Even messages you sent are piped through their servers first. |
| Outlook | |
| Spark Mail | Spark Mail for Android Devices and Windows 10 accesses your account details directly through your device and intermittently through Google-hosted Cloud servers. See also https://sparkmailapp.com/legal/privacy-app , section "OAuth login or mail server credentials". |
| Sugar Mail | Sugar Mail for Android devices uploads all account information to Servers on Linode Cloud services. |
Whitelist - feel free to use any of these vetted software packages
| Where | Whitelisted software | Remarks |
|---|---|---|
| Notebooks, PCs, Linux, Windows, Macosx | Thunderbird | A master password must be used. Without it, passwords in Thunderbird are stored in a way which gives no more security than plain text and can easily be read with tools like https://github.com/unode/firefox_decrypt |
| Linux Notebooks and PCs | Kmail, Evolution, Claws mail | |
| iPhone, iPad | IOS included apps | |
| Android phone or tablet | FairEmail | Very privacy focused mail client. |
| Gmail |
FAQ - Access, Security
How do I access the institute email account?
Permanent Link:Every institute user is assigned a mail account which includes an address and a calendar management system. The address is
[loginname]@cbs.mpg.de (i.e. mueller@cbs.mpg.de )
There are several way to access your account:
| Method | Pros | Cons |
|---|---|---|
| Web browser | No setup necessary - just visit the website. | Internet connection is mandatory. There is an offline-mode available but it's not useful, if there's a lot of content in the mailbox. 2-factor authentication is required for that. |
| Client software | Handling multiple email accounts in one place is easier. Mails are stored locally and can be managed without an Internet connection. |
Local program is necessary. |
Web browser
The email account is accessible via any browser at this address: https://mail.cbs.mpg.de Have your smartphone ready since you might have to enter a TAN as a second authentication factor.IMAP client software
Permanent Link:IMAP is the language, most email applications and email servers are able to speak. Most email applications will auto detect necessary parameters. You'll just have to enter your full name, your email address and a newly created application password. Find recommended software at Groupware.
Manual email client configuration
If your email app doesn't automatically detect the necessary parameters, here they are:- Protocol for accessing mails:
IMAP4orIMAP(more precisly:IMAP4s). - IMAP4-Server:
mail.cbs.mpg.de- Security type:
TLS(sometimes called SSL or implicit TLS; "Starttls" is always the wrong choice!) - Port number:
993 - Username: Your institute login name (e.g.
schmidt) - Password: You're going to have to create an application password.
- Security type:
- Server for sending mails
mail.cbs.mpg.de- Security type:
TLS(sometimes called SSL or implicit TLS; "Starttls" is always the wrong choice!) - Port number:
465 - Username, password: Same as for IMAP4
- Security type:
- Calendar-Server:
https://mail.cbs.mpg.de- Username, password: Same es for IMAP4
macOS/iOS email app and calendar
Permanent Link:To simplify macOS PIM setup with a configuration profile:
- Remove any existing account connections from macOS/iOS, if you have any.
- Create an application password via the email server's Web GUI.
You'll need to copy and paste the password later. Do not write it down anywhere! It is a security feature of application passwords that they are only remembered by applications - not by humans. - Open Safari and go to https://ac.cbs.mpg.de . Use the upper form, type your user name and download the profile.
- In System Preferences, under Security, install the profile using the application password you created in step one. You'll have to enter the password multiple times. Forget the password after that, do not write it down! You'll never need it again.
- Log into the email server's and create an for this macOS computer.
- Wait for your mailbox to sync with your computer.
How do I use encryption or digital signatures?
You'll need a digital identity for digital signatures and to receive encrypted emails. Handling digital signatures or encrypted Emails is not possible in the Webgui. You'll need an Email application for that.Application passwords - How do I use 2FA with email/calendar software?
Permanent Link:Regular email software is unable to handle two-factor authentication. The Solution is to create a random longish password in the Zimbra GUI—one per email client instance. You can later remove access for certain email clients or add new ones at will. The process is explained here.
Why am I sometimes logged out of the Web GUI without explanation?
Permanent Link:When logging into the Web GUI, your browser receives a secret number (an "auth token") which is then used to identify your browser when communicating with the Web GUI. This token is time limited. It will survive restarting the browser or even your computer after which you can continue working in the Web GUI. However, after 22 hours it's invalidated and you have to re-login. This is common practice when it comes to Web sessions.
My account is suddenly inaccessible and I cannot re-login.
Permanent Link:Possible reason 1 - Temporary lockout (Very likely. Our email server blocks around 5 accounts per day.)
When the email server detects too many failed login attempts for a given account—more than 10 failed logins in 10 minutes—the account is blocked for 15 minutes. All sessions (graphical ones and data connections i.e. from mobile phones) are terminated. There are multiple possible reasons for a temporary lockout:- You changed your password and one of your programs or devices is still using the old one. Solution: Make sure, all of your programs and devices have the correct password.
- You re-activated an old device (e.g. a phone or laptop) you didn't use for a long time. The solution is the same as in (1).
- An evil person tried to guess your password with a high frequency. In this case, the temporary block is protecting your password. Solution: You'll have to wait 15 minutes.
Possible reason 2 - Phishing success (Very unlikely since 2FA was introduced)
You might have noticed these emails insisting on you entering your credentials on some server to- "update your account"
- "increase your quota"
- "unblock your account"
- ...
Possible reason 3 - Account timeout (Likely)
When your institutional account expires, you will retain access to your email account for an additional three months. You will receive an email detailing this information. After the three-month extension, your account will be deactivated, and your login credentials will no longer be valid. Solution: You have to get your account renewed by Administration. IT can't help in this case.I have two or more phones. Can I use either one for 2FA?
Permanent Link:Absolutely. Google Authenticator has an Import/Export function. You can export your 2FA credentials from one into a QR code and import it via camera into the other. This is perfectly safe. Just make sure to:
- Not have the credentials (e.g. QR code) as a file somewhere.
- Come to IT to reset 2FA if your phone is lost so no one else owns valid credentials of yours.
The generated TANs don't work (anymore). What's wrong?
The 2FA-TANs are calculated from two pieces of data:- the secret password you entered into Google Authenticator and
- the current time.
- Click on the three dots in the upper right corner in Google Authenticator.
- Select "preferences".
- Select "time correction".
- Select "synchronize now".
- Google Authenticator will now fetch the correct time from the network and use it for generated TANs. This doesn't affect other apps.
What if I loose access to my TANs?
Permanent Link:If your phone is lost, broken or you accidentally removed Google Authenticator, you cannot create TANs anymore - which will prevent you from logging into the email server's Web GUI. However, email applications equipped with application passwords will continue to work. If you do not have your seed code, please contact IT. You'll need to
- call a core IT member that knows you personally and is able to identify you. IT staff may refuse this method if there is any doubt about your identity.
- or come to IT physically and present a valid passport, Personalausweis or Aufenthaltstitel.
Why do I have to use Password and/or 2FA every time I login? (How to save some time)
Permanent Link:By default the Web GUI expects a 2FA TAN being entered every time you log in. However, there are two check boxes in the login process:
- Do not check these check boxes on public computers (e.g. in a public library) or on other people's devices, like a friend's laptop!
- You can safely use both check boxes on your personal laptops and whenever you have a personal account on a computer—e.g. in the institute when logging in using your credentials. Don't worry, it's not actually the computer that's being trusted but your user account. The next person using the computer will not be able to impersonate you.
- The trust can be revoked in the "Preferences"/"Accounts" section of the Web GUI.
- Persistent cookies are being used for both trust functions. If you have privacy options enabled which clear cookies in your browser, you might want to add an exception for the email server's Web GUI.
FAQ - Misc
Why is there so little storage in my mailbox?
Read about that here.How do I free up space in a mailbox?
Space in a mailbox is almost exclusively used by big attachments and by mails containing large images. It's good practice to save important attachments to your computer's file system and removing them from the mail server. The mail itself will remain on the mail server, requiring less storage.- Find big mails
- Go to the search field on top of the web interface and type
larger:100KBto find all mails that are larger than that value.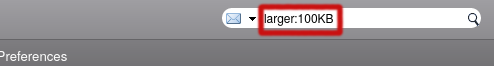
- Go to the search field on top of the web interface and type
- Prepare a sorted list
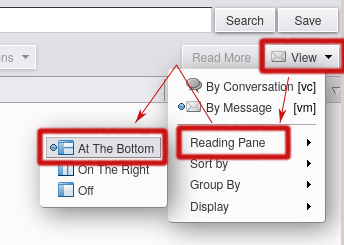
- Make sure the right listing mode (one that shows a mail's size) is selected. This only has to be done once.
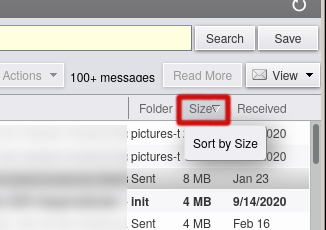
- Sort the list by size descending. This way you can start with the biggest ones and work your way to to smaller ones.
- Make sure the right listing mode (one that shows a mail's size) is selected. This only has to be done once.
- Remove things
- Now you can either directly remove big mails or download/remove their attachments (either single ones or all at once). There are remove-links for each attachment and there's one link to quickly remove all of them.
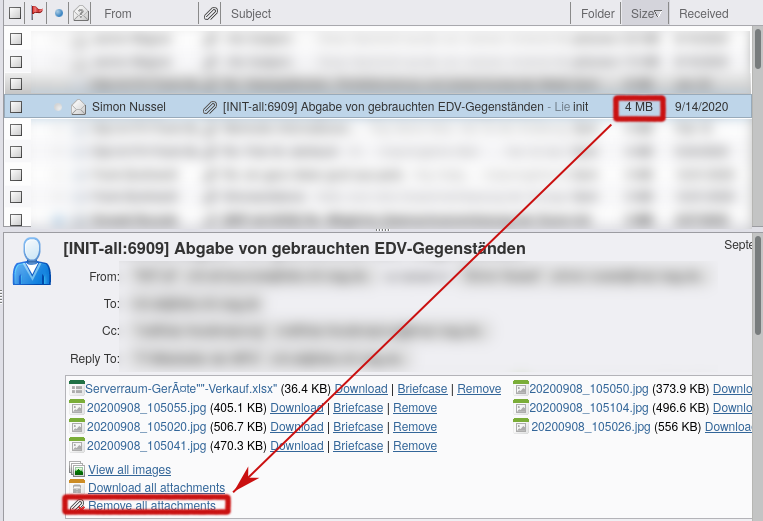
- Now you can either directly remove big mails or download/remove their attachments (either single ones or all at once). There are remove-links for each attachment and there's one link to quickly remove all of them.
I (accidently) deleted an email. What should I do?
Permanent Link:The email server is the best backed-up system in the institute. If you're unable to restore an email, please contact IT. There are several levels of "being deleted" an email has to go through to actually be removed. Find them below.
Trash bin
Deleted emails go to the Trash folder first and can be retrieved easily from there. Just drag and drop them to a folder of your choice. Emails in the Trash folder are automatically deleted 30 days after they are moved there. Hint: Trash is for items you delete; Junk is for spam automatically filtered by the email service.Dumpster
Emails removed from Trash stay in the "dumpster" for some days. The dumpster is not a folder but an area visibly in the Web GUI by selecting "Restore deleted Items" from the Trash folder's context menu. There's no way for you to remove emails from this area. The email server will permanently delete emails from the dumpster 30 days after they were moved there. Hint: This function works as a safety net against rouge email software. Email software is able to circumvent the Trash folder but not the dumpster.Backup
Institute emails are stored on the server for weeks. To recover an email:- Create a ticket containing the desired restoration time.
- For example, if an email was deleted at 10:30 on 01.05.2015, request restoration from 10:15 on that date.
- IT can only restore the entire account at a specific time, not individual emails.
- IT will restore a backup, adding it to your account as a folder.
- Find and retrieve your email(s).
- Inform IT when done to remove the backup folder.
I'm leaving the institute. What happens to my emails?
Permanent Link:- You'll be notified of the deactivation date via email before your contract expires.
- Your email account will remain active for three months after your contract ended.
- Consider setting up email forwarding to another address (e.g. to your new research facility or to a colleague remaining at the institute).
- Backup your emails using an email client software or the Web GUI's Import/Export feature under Preferences to get a downloadable archive file.
- After three months, your email account and all contained data (email, calendars, ...) will be deleted:
- If a mail forwarding address is set, it will remain in place for 21 additional months.
- Aliases assigned to your former account will be disabled at this point. Attempting to send emails to those will then cause an "unknown address" error message.
- You won't receive emails from internal mailing lists.
- Post-deletion, setting or changing forwards requires an in-person visit to IT with identification.
How can I forward emails to another email address?
Permanent Link:Warning: German law applies to the institute's mailserver. If there's a chance that you receive mails from test subjects or patients, you have to make sure, not to send these mails outside of german jurisdiction since this would violate german privacy law . Examples of mail services in other jurisdictions are:
- Googlemail
- Hotmail
- Got to the Webgui
- Select the "Preferences" tab
- Select the "Mail" configuration block on the left
- In the paragraph "Receiving Messages" ...
- ... enter the target address of your choice and select the "Don't keep a local of messages" checkbox.
My account is already locked so I cannot create the forward myself.
You have to come to IT with a passport or a Personalausweis since we cannot be certain of your identity any other way. We have to be very strict here. IT will not accept forwards request via phone or an email from a non-institute email account.Can I get a mailing list?
Absolutely. Follow these steps:- There are 3 types of managing the members of a MailingLists. Choose one.
- Think about a name. It must contain a Dash sign (
-) to clearly distinguish it from user accounts that exist in the same name space. - Please write a ticket to request the mailing list.
- IT might have technical objections about the name. Those would then be communicated via the ticket system.
 Copyright © by the contributing authors. All material on this collaboration platform is the property of the contributing authors.
Copyright © by the contributing authors. All material on this collaboration platform is the property of the contributing authors. Ideas, requests, problems regarding Foswiki? Send feedback